Spookypass
2025-01-16
INTRODUCTION
Super easy challenge. This challenge introduces a beginner at reversing into opening their tools and checking inside a file.
FIRST TAKE
Start by downloading the file. We can check file to see the file type:
./pass: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=3008217772cc2426c643d69b80a96c715490dd91, for GNU/Linux 4.4.0, not stripped
Try running the executable. It presents you with a simple prompt, asking the password:
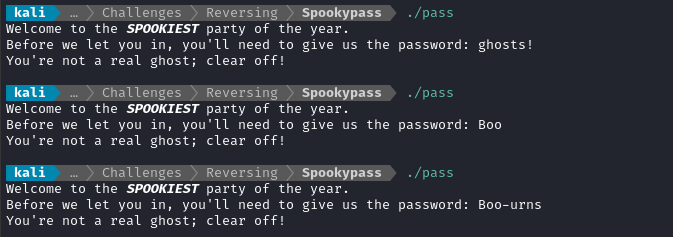
SOLUTION
I’ll be using Binary Ninja to decompile the encryption program. Thankfully, it does a very nice job of laying out the code.
Reader: if you haven’t tried Binary Ninja yet, go try it! It’s free, cross-platform, and very high quality.
For similar challenges, I’ve used
Ghidra,Ida, andRadare2. My main takeaway is that Binary Ninja has very similar functionality but is far, far easier to operate. There’s even a cloud-based version so you won’t need a local installation.
C programs tend to have a bunch of constants defined near the beginning, up in the big grey splotch at the top (it ends at roughly 0x310):
However, this program didn’t seem to have anything up there.
Recalling that this is a “very easy” challenge, I figured I’d just search for the flag directly. Click the little magnifying glass icon (I’m on the desktop version of Binary Ninja) to open the Find pane:
Select Text and enter a search term. I searched for the typical flag format HTB{. Right away, we see a result at address 0x4060:
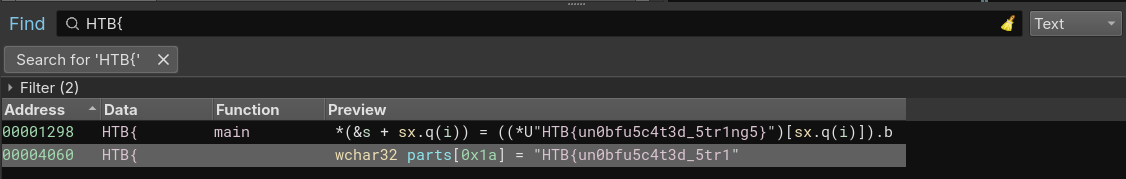
Very easy, indeed! 👍
LESSONS LEARNED

- Start with the obvious stuff then work up from there. As long as you have the right tools on-hand, a lot of problems become pretty easy.
Thanks for reading
🤝🤝🤝🤝
@4wayhandshake
